If you haven’t already heard about it, Meltdown and Spectre were publicly revealed in 2018 as three security threats taking advantage of vulnerabilities in most CPUs made since 1995. Two of the threats are named together as Spectre, the other is Meltdown.
The flaws were discovered in 2017, and are based on two techniques used to provide performance features to computers, speculative execution and caching. By exploiting the vulnerabilities a malicious program can gain access to your information that it shouldn’t be able to.
Speculative execution is when the CPU takes a guess on what a program wants to do next so it is already done when the program asks it to perform the calculations. Caching stores data from memory in some smaller but high speed memory inside the CPU so the CPU can access it much faster. Normally the data in the CPU’s cache memory is protected, but speculative execution happens before security checks occur to know if it is allowed to use the data.
Why are they dangerous?
Meltdown allows a program running on a computer to access data on the computer, regardless if it is for that program or another one. It doesn’t need much knowledge about the programs it is attacking, and is easy to use. Because it looks at data in the CPU cache, it can see data even if it is from another virtual computer running on the same server hardware. Virtual computers are a common way to have multiple servers running on one physical computer. It “melts” hardware enforced security boundaries.
Spectre requires more knowledge of the program being attacked, and doesn’t attack data from other programs. However, it works on just about any CPU built, including mobile phones and tablets. Spectre can be exploited from JavaScript in a web browser, as well as in many other ways. It is not known if Spectre can be resolved with updates alone and may require new designs and new CPUs to resolve fully. The ways Spectre can be exploited are expected to continue to surface and “haunt” us for years to come.
Is my computer affected?
Most likely, yes. These are basically a hardware problem, so they can’t be fixed with a simple software patch. Some software can be patched to offer protection on an affected computer, such as web browsers.
There are no known threats taking advantage of these vulnerabilities (18th Jan 2018), but now it has been published it will only be a matter of time.
A malware called Smoke Loader is being offered as an official patch, but actually releases malware onto your computer, potentially worse than the Meltdown and Spectre vulnerabilities themselves.
There are a lot of releases of patches already released. A Linux patch last year to improve Linux security is not related, but incidentally provides protection from Meltdown. Intel, Microsoft, Google, and Apple have made available security patches to protect you computer.
Some patches could mean you loose performance, especially if the patches are not hardware patches. Speculative execution and caching are for boosting performance, so restricting their functionality will result in performance loss. A BIOS update will be required to properly protect your computer.
How do I check my computer?
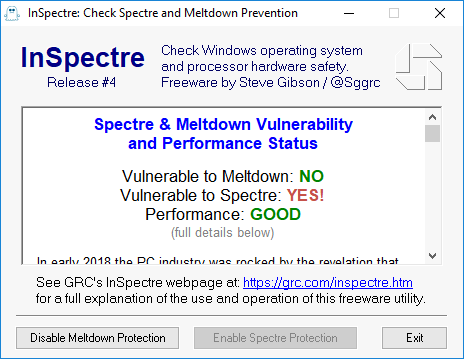
To check if your Windows computer is affected, Steve Gibson from Gibson Research Corporation (GRC) has released a free utility called InSpectre. It will tell you if your computer is protected from the Meltdown and Spectre vulnerabilities. The screenshot at the top of this article is from one of my own computers before installing BIOS updates.
Go to GRC’s website and download InSpectre. Do not use the Disable Meltdown Protection or the Disable Spectre Protection buttons.
How do I patch my computer?
Security patches released by Microsoft for all windows since Windows 7. If you install security updates regularly, then you possibly already have some protection. Some 3rd party anti-virus software have not provided updates to allow Windows to install the updates.
Security researcher Kevin Beaumont has created this public document to check if your anti-virus software is updated and supported.
The patches come with an impact on performance, but if you run Windows 10 on modern hardware the impact will likely be unnoticed. Windows 7 and 8 work differently and rely on these features more, so the patches will possibly be noticeable. Older generation CPUs are also impacted more, especially if your computer is bought before 2016.
Using InSpectre’s Disable Meltdown Protection and Disable Specture Protection, the performance impact will be removed, but it will also remove the security protection. Unless you are a professional who understands the consequences and risks of disabling protection, it is best to leave it alone.
How to update your BIOS and Intel drivers is harder to describe, as it can be different for every computer. If you have Microsoft Surface products, these will come through in the normal Windows Updates for most models.
Intel plan to make updates available for all of their CPUs released in the last 5 years by the end of January. They will then work on updates for older CPUs. This doesn’t mean they will be released by your computer manufacture however, as it is the manufacture who is responsible to test and release the updates for their computers. For example, Microsoft are not updating all of the Surface products, with older models missing out.
It is best to go to your computer manufacture’s website to check what updates are available for your computer. For my Dell workstation, laptop and tablet, I went to the Dell support site and clicked on the Detect PC button, and it gave me a list of all the hardware and driver updates available for my computers, including BIOS updates, and chipset updates.
Should I buy a new computer instead?
This is a difficult question at this time, but I wouldn’t rush into it if you don’t otherwise have a need to upgrade. There are no known exploits of these vulnerabilities yet, and updating your browsers will help make things safer (Edge and Internet Explorer already have updates, Chrome and FireFox updates are due 23rd January).
Manufactures are already unveiling new products ahead of CES 2018, and these have the vulnerabilities. New hardware without the vulnerabilities could be another year or two before we can buy them.
Updates are still being released, and even those that have been will possibly have more updates to lessen any performance impacts from earlier updates. New stock on shelves that already have the updates installed won’t be seen for some time, and could be many months before shelves don’t have stock without updates.
This question may be easier to answer in 2019 or even 2020, if new hardware is announced without the vulnerabilities. For now, if you were thinking of buying a computer soon then you might as well do so. If you wait 6 months you may get one that is already updated.
If your computer is more than 5 years old, you may never see an update, other than the operating system updates. If you are on XP, then you definitely won’t get any updates, and you are probably overdue to update your computer.
Rubidyn
Are you in the Redcliffe area, Moreton Bay Regional Council, or north side of Brisbane? Rubidyn may be able to help you install updates on your computer. Send us an email with details of the computer/s you have and where you are located and we can send you a quote to update.
